For the last several years, the news has been plagued with scary headlines about uncrackable ransomware, millions of clients’ data exposed, and businesses forced to close or change management due to lack of compliance or a failure to meet the bare minimum for IT security.
Most recently, UBER revealed it had experienced a data breach of 56 million users and back in September, the Equifax hack shone light on how under-prepared even some of the largest companies can be. 143 million US customers’ data was accessed and it was four months before the company even noticed the intrusion.
The average small to medium-sized business may not face the most aggressive of these threats but if they’re not prepared, the cyber attacks they do face can be just as deadly. Here is a quick list of prevalent cyber threats and how to address them.
Malware and Ransomware

There are several types of malware, including ransomware and spyware. This malicious software can steal your data, make it inaccessible, ransom you for it, and other damaging outcomes while pretending to be a trusted program.
Most malware downloads arrive by email in links or attachments. Often disguised as a trusted source, it will take you to alleged system updates, familiar program installs and other prompts that look harmless that will keep you clicking through until the malware is installed in your system.
Take the new Locky ransomware variant as an example:
“According to security researchers at Comodo, who detected the new spam campaign, this is a “large-scale, email-based ransomware attack in which a new Trojan malware variant appears as an unknown file and can slip into unsuspecting and unprepared organizations’ infrastructures”.
What You Can Do:
At a company level, make sure every employee knows what to look for and has a base level of knowledge about these types of cyber threats. Ensure you have a trusted anti-virus that someone regularly checks is functioning properly. At the individual level, never click on links or open attachments from sources you don’t recognize. If your device is prompting you to do something suspicious, use your intuition and reach out to your IT support person or service provider.
A secondary precaution and best practice is to have a full backup rotation in place. If ransomware has infected your backups you may have to go further back in history than just the most recent backup. Include this as part of your disaster recovery plan so that those working to restore your systems know in advance what they might be facing.
This is a crucial component of your IT environment that allows you to continue providing services in the face of disaster, be it ransomware or water damage knocking out your on-premise systems.
Phishing and Spear Phishing Attacks

Phishing attacks usually arrive by email, social media, or some form of communication where they will pretend to be a trusted source and trick the user into sharing sensitive information such as login credentials, payment information, and other info that can be used against the victim. They are ‘fishing’ for passwords.
With regular phishing, you could say that hackers are sending out a massive net, hoping to capture as many victims as possible with a general deception and then leveraging those accounts and information for their own purposes. Like this Google login page example from our previous post:
![]()
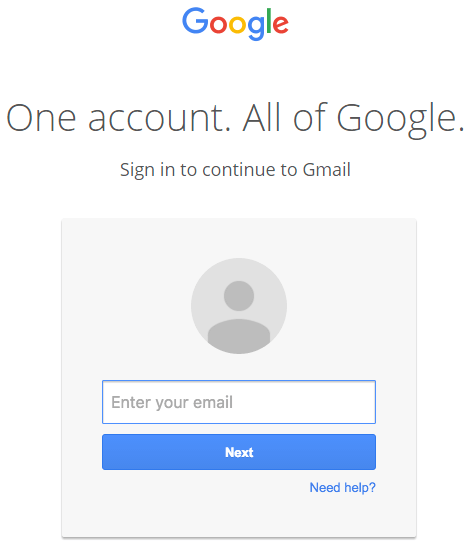
Image source: https://www.wordfence.com/blog/2017/01/gmail-phishing-data-uri/
Without looking at the URL, you may never realize that the page you are on isn’t your usual Google login page.
Spear phishing is an attack where hackers target specific individuals and organizations, gather background info, and then try to gain access to their systems or extract some sort of payment using messages customized to what they’ve learned about the person. It is the most common way an intentional piece of malware is deployed to an organization.
This is especially dangerous for smaller organizations who can be leveraged as a stepping stone to gain access to their larger clients, partners, or affiliates. From a Trend Micro report, 91% of cyber-attacks are initiated by a spear phishing email.
What You Can Do:
Education on what these threats look like is the most important thing you can do. Check the sender’s email address, the URL of the pages you are logging into and limit the places your email address and contact info appears to where it is critical.
Limit the number of people with admin rights and ensure the people with these privilege levels know what to look for when it comes to suspicious activity. Use two-factor authentication where possible.
Employ web and email protection tools for all types of devices that your organization uses: mobile, desktop, and any other connected device.
Social Engineering Attacks
A huge part of what makes the above cyber threats so dangerous is that they use social engineering to trick people into unwittingly superseding or working around the security measures that your organization has put in place. This ties into all the above tactics and the best way to prevent it is through ongoing education on what these threats look like and how to deal with them once they’re identified.
Vulnerable Apps and Software

Applications your organization uses need to be updated routinely and monitored for any sort of malicious activity. Updates are rolled out to fix any security flaws that are later discovered and if you’re not patching these holes in security, your apps and the systems attached to them can be at risk.
Any app that your business uses can potentially be a risk to intrusion if it is vulnerable and not well-maintained. That includes your website, mobile and IoT apps, software installed on mobile devices, and third-party applications.
A popular security app, CCleaner was recently hacked and used to deliver malware to its users. The company, Avast, eventually discovered it and released an update but at that point, a large portion of their customers had already been exposed for nearly a month.
What You Can Do:
Keep track of all your digital and physical assets and ensure they are safely updated when it is the right time to do so. Limit the number of third-party plugins and apps you use and make sure you’re on the most current, supported version.
Task someone to routinely check for new versions of apps and programs your organization uses and update them. Patching is an undervalued skillset and not something that every business can do for their own applications. If you need guidance on patching or want to find out where to start, you should consult a business that has experience with patch management. We can help you determine if it is something you can handle in-house and what steps you’d have to take to manage the patching effectively. Conduct a vulnerability assessment to uncover any weak points in your network, websites, apps, and other digital assets.
Other Dangerous Cyber Threats
Distributed Denial of Services (DDoS): Overloading your website, application, or systems with requests for information, typically from many infected computers.
What You Can Do: Routers and firewalls help reduce much of the threat. If your business relies on delivering an online service and you’re still concerned, there are specific DDoS mitigation appliances and services you can employ to further protect your organization.
Brute force attacks: Rapid-fire attempts to try gaining access through public facing logins such as a website or portal.
What You Can Do: Take measures to limit login attempts, make more sophisticated passwords, and lockdown logins by IP address if that is a method that works for your business.
Advanced Persistent Threat (APT): Someone gains access to a network via spear phishing or some other means, stays there for a long time, then leverages that access to create backdoors and more opportunities for intrusion. Often times you won’t know the extent of the damage until a data dump is released as CNS Group highlights in their article: Shadow Brokers Leak – What Lessons Have Been Learnt?.
What You Can Do: Monitor systems for suspicious activity and data leaving the company’s networks going to unknown sources.
The best way to address these potential cyber threats is to undergo a comprehensive IT security assessment to address the current state of your security, identify if there are any gaps, and create a strategy for bringing them up to speed.
If you’d like to speak with our IT experts about what this would look like, you can request a free 30-minute consult to discuss.
[]








