As you may already know, October is National Cyber Security Awareness Month (NCSAM). We are in the final week of it and the theme for Week 4 is: Our Continuously Connected Lives: What’s Your “Apptitude”?
This is the 13th Annual NCSAM and National Cyber Security Alliance along with many industry groups, associations, businesses, and professionals have been educating people on the cyber threats to look out for and how organizations and individuals can protect themselves.
Cybersecurity topics that have already been covered in the first few weeks included:
- The Basic Steps to Online Safety and Security
- From the Break Room to the Boardroom: Creating a Culture of Cybersecurity in the Workplace
- Recognizing and Combating Cybercrime
To see the full descriptions on these topics, visit About National Cyber Security Awareness Month.
Cyber Threats in 2016
2016 has been a year of non-stop ransomware, insider leaks, and all sorts of cybersecurity threats for governments, businesses, and organizations of all sizes. Some notable cyberattacks and attempts on large companies includes:
- Microsoft receiving more than 10 million cyberattacks per day on its online infrastructure
- Yahoo getting hacked and opening up over 500 million users account details
- Dropbox and LinkedIn confronting hacks from 2012 as the list of usernames and passwords became available this summer.
- And 20 more large name companies that were breached one way or another since the start of 2016.
If you’re worried that your user information may have been leaked, you can enter in your email address on HaveIBeenPwned.com to cross check more than 500 million accounts from over 100 compromised websites. If you’re a business that has been hit by ransomware or you fear there’s been a data breach and you’re looking for next steps, contact us immediately.
However, it’s not just large companies that have to worry. In fact, 20% of small to mid-sized businesses have been cybercrime targets and the number continues to grow year-over-year. Since smaller organizations like non-profits and educational institutions often have reduced budgets for things like cybersecurity, they happen to get targeted more often and are less able to deal with the outcome. IT security professional have described small businesses as being in the “sweet spot” for hackers as they have more online resources that can be accessed than an individual user and less protection than larger companies.
Most Cyber-Attacked Industries
According to IBM, the 5 most cyber-attacked industries in 2015 are:
- Healthcare
- Manufacturing
- Financial Services
- Government
- Transportation
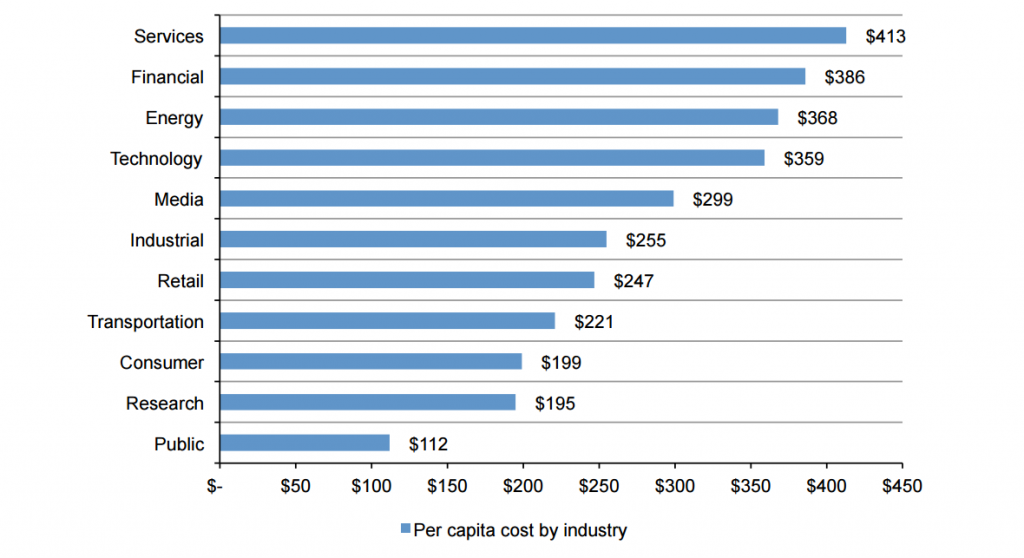
These are industries where a lot of valuable and private information is stored about people’s health, financials, and personal records. In June, Ponemon Institute released a report called 2016 Cost of Data Breach Study: Canada. They found that the average cost of each stolen or lost record is $278 and the average total cost of a data breach for companies in Canada is $6.03 million.
Per capita cost of data breaches by industry
(Measured in Canadian dollars) Image source: http://www-01.ibm.com/common/ssi/cgi-bin/ssialias?htmlfid=SEL03094CAEN
What You Can Do
As an Individual
Create strong unique passwords for each account. Re-using the same password opens up all your accounts if one is breached and your login credentials are leaked.
Stay up-to-date on what current cyberattacks look like and how to prevent them. You can’t defend yourself from what you don’t know. Try out The Ultimate Phishing Quiz from Intronis to see if you can determine which email and links are actually malicious.
Inform others as well about what to look out for. If you know that family members or friends aren’t as tech-savvy, clue them in to what the most dangerous trending cyber threats are.
Trust your instinct. If a website, email, or link seems suspicious, don’t click on it.
The NCSAM theme for Week 4: Our Continuously Connected Lives: What’s Your “Apptitude” touches on a really good point as well that we are no longer only connecting to networks via more traditional machines like desktops and laptops. You’ve got to make sure your phones and tablets are protected as well. It is also critical you understand what connecting your wearables and other internet-connected devices means for security and privacy.
As a Business
Ensure you have a cybersecurity plan. National Cyber Security Alliance lists these three key areas to focus on:
- Prevention: Solutions, policies and procedures need to be identified to reduce the risk of attacks.
- Resolution: In the event of a computer security breach, plans and procedures need to be in place to determine the resources that will be used to remedy a threat.
- Restitution: Companies need to be prepared to address the repercussions of a security threat with their employees and customers to ensure that any loss of trust or business is minimal and short-lived.

Education for Employees: Educating and informing employees on what to look out for is a crucial step in prevention as well as resolution of cyberattacks. Publish cybersecurity tips to your company’s intranet and bring up cybersecurity policies during onboarding new employees or at company meetings.
Keep Software Up-To-Date: Attackers will try to exploit any vulnerability in your business software. That’s why there are so many patches and updates that get released. If you don’t keep your software updated, it can open up your network and systems to entry by malicious bots or hackers.
Firewalls and Antivirus: Have tools in place to scan for any malware or other dangerous files on your system. Make sure both your company’s infrastructure and software are protected. Any part of your IT set-up that isn’t protected allows attackers an opportunity to get in and wreak havoc.
Disaster Recovery and Back-Ups: Make sure you routinely back-up your system and test that it works. If your business encounters a ransomware threat, you need to know that you can get your system up and running again quickly without relying on paying a ransom to an anonymous attacker in the hopes that they return access to your data.
Website and App Security: Company websites and apps are often targeted as entry points for hackers to try and access company and customer information. Make sure you have tools and processes in place to protect and monitor for any attempts to access. A web vulnerability assessment done by a third party is a good way to ensure there aren’t any doors left open for hackers.
Assign Appropriate Levels of Permissions: Insider threats can be both intentional and accidental. By limiting who has access to information to just the people that require it, you reduce the chances that someone accidentally shares it or loses a USB or laptop with access to confidential information. It also reduces the ease at which an insider looking to leverage company or client info can access and share it.
No matter how many precautions you take, personal accounts and businesses aren’t safe from cyber threats but you can drastically reduce the chance of it happening to you and the amount of damage that can be done if it happens. With the aggressive increase in number and types of cyberattacks, its best to entrust your business’ data with professionals who have the extensive knowledge and resources necessary to ensure you’re not a victim of these types of attacks.
If you want to make sure you’ve covered all the bases when it comes to cybersecurity in your IT strategy, request a free consult from our Managed Services experts. We can highlight potential problem areas and see if there is an opportunity to work together to close any gaps.
[]